With more and more similar cybersecurity incidents occurring in OT systems, business owners and regulators are keen to seek solutions that enhance industrial cybersecurity and allow businesses to keep functioning normally. In our previous articles, we have talked about the defense-in-depth concept that allows you to leverage the existing network infrastructure and investment to build the first line of your network defense. In this article, we will share the best practices, in which we collaborated with our global customers, to safeguard their critical infrastructure–the energy storage system for the renewable energy sector.
When it comes to renewable energy, we often think of solar or wind farms that bring cleaner electricity to global citizens. It is a great initiative that keeps driving the global economy while reducing carbon dioxide emissions. The public and private sectors are both working together to move toward this healthier future. However, one of the shortcomings of renewable energy is the difficulty of matching supply with demand. The sun does not always shine when the community needs electricity during peak periods and the wind does not stop blowing during off-peak periods. One of the best ways to stabilize the power grid and offer a steadier power supply is to use batteries that can store surplus power when the supply is high and can discharge power when the supply is low.
Security Challenges of an Energy Storage System
What Is an Energy Storage System (ESS)?
An energy storage system can convert electrical energy that is generated into a form that can be stored. A common example of energy storage in the renewable energy sector is the rechargeable battery. A typical ESS in a wind or solar farm consists of the energy management system (EMS) and the power plant controller to monitor and control operations of the ESS in real time. The power plant controller aggregates the data collected from the power conversion system (PCS) and the battery management system (BMS) containers. All the equipment is placed in containers that are often deployed in harsh environments such as deserts or the Arctic where renewable energy sources such as the sun and wind are plentiful.

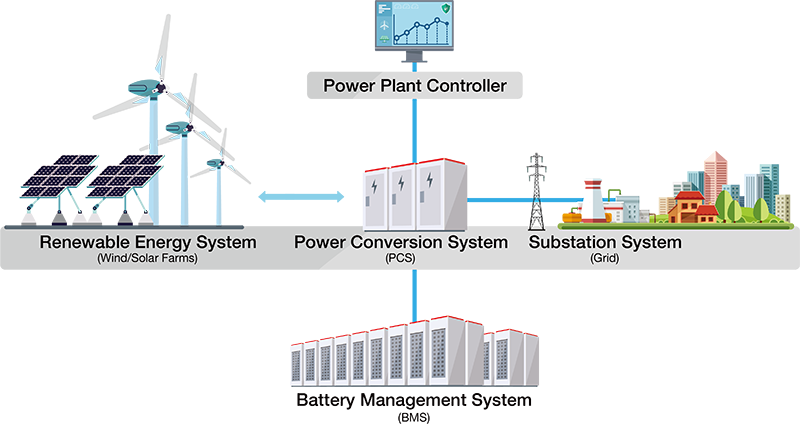
Diagram: Typical scenario of an energy storage system.
Security Challenges
The ESS, as mentioned earlier, includes multiple systems to ensure the stableness of the whole process of power storage and supply. The network communication between the EMS, PCS, and BMS needs to be protected from unauthorized access and any unwanted activity that may disrupt operations. Thus, we recommend considering the potential security risks from two perspectives. The first is the overall network security boundary: is the access authenticated and authorized, and are the commands being sent as expected? The other is the communication security at the edge: is the communication and access of the device securely protected? These security mechanisms need to be designed when containers are produced at the manufacturing sites, which allows the whole system to be efficiently delivered and connected to the farm and grid.
Best Practices on Safeguarding the Energy Storage System
To dive deeper into these two perspectives, we will look at the following case studies to understand the practices that can protect both the Ethernet and serial-based networks from the edge to the network level.
Build Security Boundaries Vertically and Horizontally
To protect the communications between the renewable energy system, the power plant controller, the power conversion system and the substation system, we suggest deploying stateful firewalls with Modbus deep packet inspection (DPI) in between.
- Vertical protection: the firewalls play an important role as a gatekeeper to protect the communication in between the systems.
- Horizontal protection: the Modbus deep packet inspection engine can examine the commands going through and drop the packets that are not authorized or not listed.
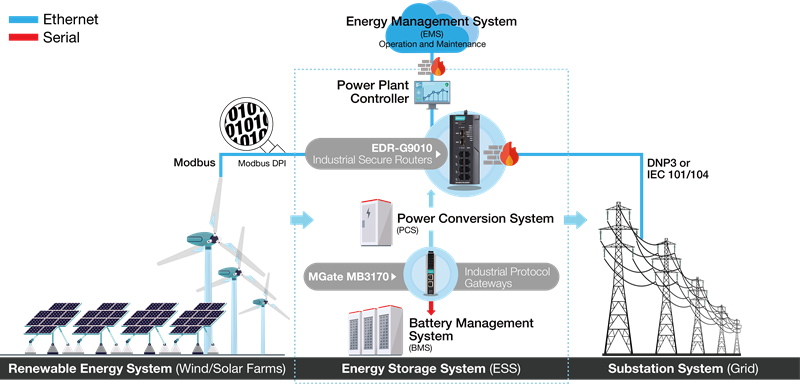
Diagram: The firewalls and Modbus deep packet inspection engine build both vertical and horizontal protection. The protocol gateway facilitates communication at the edge.
|
Tips
|
As solar or wind farms are often located in remote areas, deploying an all-in-one firewall/NAT/VPN/switch solution that features network redundancy can help system integrators efficiently design the network architecture before the systems are commissioned at the field site. The NAT function can also help manage the consistency of IP addresses for the equipment in each container, reducing the hassles that arise from conflicting IP addresses.
|
Enhance Remote Connection Security for a Li-ion ESS
To develop seamless and secure communications between an ESS and the control center, we suggest a reliable edge connectivity solution deployed in between.
- Facilitate communications at the edge: deploy protocol gateways between Modbus serial-based batteries and Ethernet-based RTUs to ensure seamless communications.
- Secure the communications: leverage security features such as HTTPS, SNMPv3 management, and Accessible IP Addresses to ensure the communication and access of the device is securely protected, reducing risks and enhancing the reliability of remote communications.
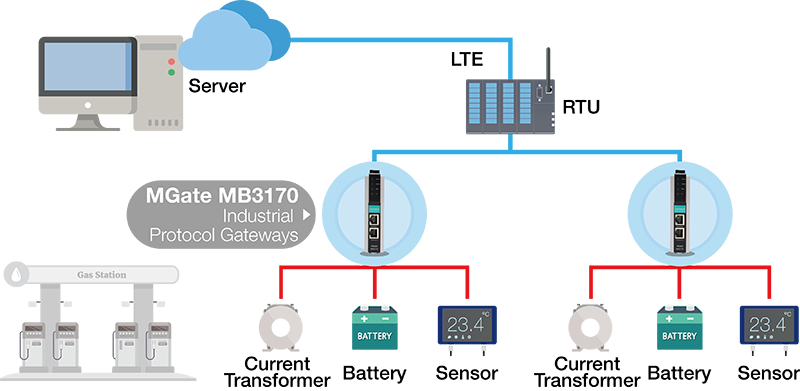
Diagram: Enhance remote connection security at the edge.
|
Tips
|
To ensure smooth operation of the ESS, you need to pay attention to several operational conditions. Information such as battery level, power stability, and environmental conditions require constant monitoring from the control center. Therefore, a protocol gateway that has easy-to-use configuration tools can help operators collect data from a variety of serial-based field devices and incorporate it into Ethernet-based systems smoothly. In addition, secure-hardened protocol gateways that feature embedded security functions with a step-by-step security hardening guide can enhance your device security with minimal effort.
|
Moxa has helped customers build secure communication and networks around the world. Download the case studies to learn more.
Conclusions
A secure and reliable energy storage system (ESS) can help expand electricity capacity of the renewable energy sector in response to the initiative of increasing the share of renewable energy and stabilizing power supply. An ESS also plays an important role to maintain the security of critical infrastructure. In light of the whole power ecosystem, we recommend securing the network and communications by defining the network security boundary to determine who can access a network and what information they can pass through it. In addition, to enhance the reliability of the power storage and management system, it is imperative to ensure the security of communications in between the devices that connect the batteries and sensors inside the containers.
The MGate Series protocol gateways provide a variety of protocol conversion options for your ESS applications. Our protocol gateways are designed based on the IEC 62443 standard to enhance your device and connectivity security when you are connecting critical field data to IP networks. In addition, our MGate protocol gateways feature easy-to-use configuration and troubleshooting tools, which simplifies device deployment and makes maintenance easier for engineers.
The EDR-G9010 Series industrial secure routers help enhance cybersecurity not just forming perimeter protection but also preventing lateral (east-west) movement of malicious or unauthorized traffic. Featuring the deep packet inspect engine, the EDR-G9010 Series can recognize industrial protocols such as Modbus TCP/UDP and DNP3 traffic to protect the communication between the ESS and substation.