Looking back on 2021 so far, it is not surprising that cybersecurity-related keywords have increased in popularity on Google Search according to the global Google Trends index. Among these keywords, ‘cybersecurity boot camp near me’ and ‘cybersecurity executive order’ are being searched for with greater frequency (Google Trends as of September 2021). It can no longer be denied that cybersecurity is a popular and important topic. It has been noted that cybersecurity is like a puzzle composed of different pieces that we need to understand and it is not a subject that we should delay giving attention to.
According to a report from Deloitte, 4 out of 10 manufacturers that were surveyed have experienced security incidents, with 86% of these stating that their industrial operations were disrupted. As the OT/IT convergence trend continues to gather pace, there are several attack surfaces emerging in industrial control systems. Although some of these are known vulnerabilities, there are also some that are unknown. Therefore, everyone from management to each individual user needs to join forces to enhance industrial cybersecurity from the edge to the cloud. In this article, we will consider some practical tips recommended by different industry experts to help organizations start their cybersecurity journey.
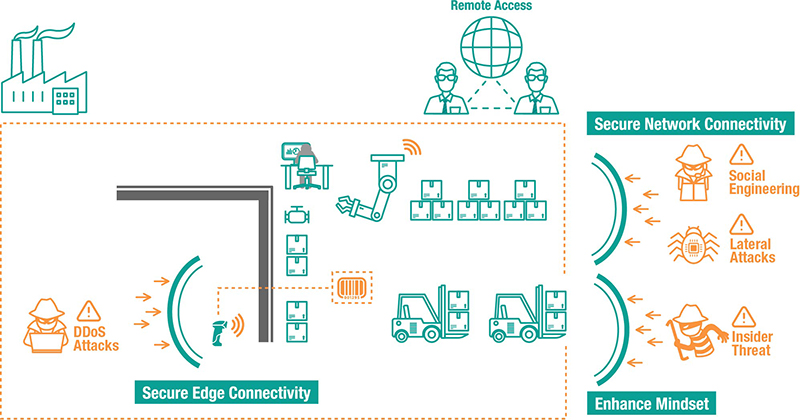
Diagram: New and Emerging Surfaces Can Be Subject to Cyberattacks in Industrial Control Systems
Tip 1: Deploy Secure-by-design Networking Devices and Set Up Devices Securely
Typically, industrial operations include a variety of legacy devices that are becoming increasingly vulnerable, as field networks are no longer always air gapped. In an ideal world, legacy equipment can be upgraded quickly with advanced solutions that have security features embedded into them. However, budget restraints and the requirement that industrial operations do not experience downtime, frequently leads to a mixture of old and new equipment operating together. When this scenario arises, it’s important to have a security-hardened networking device to enable connectivity for legacy devices. In order to ensure that the devices use a secure-by-design methodology, it is advisable to check that the embedded security functions of any networking devices adhere to security standards such as those detailed in the IEC 62443 standard. After confirming this, devices can be set up securely. For instance, we recommend disabling any unused ports and services to minimize available entry points for intruders. Here are some more tips on how you can enhance edge security and our case studies showcase Moxa’s solutions, which can help secure edge connectivity.
Tip 2: Divide Networks Into Multiple Segments
Once the network nodes are configured securely, the next step is to segment the networks following a zone and conduit policy. Dividing the connected networks into segments to enhance network security helps avoid the scenario where the entire network experiences downtime due to a single network node being compromised. Gary Kong is an OT security consultant who works at YNY Technology, which provides industrial automation solutions and consultancy on digital transformation. Gary shared his experiences helping customers ease security concerns when their OT and IT networks converge. ‘It is recommended to have a secured network architecture design, such as network segmentation or a Demilitarized Zone (DMZ), to reduce the risk of threats emerging from the IT network.’
However, it’s also important to choose the right solutions to divide industrial networks into segments. ‘Our customers understand it is not sufficient to protect an OT environment by simply placing an IT firewall in front of the OT network. However, this advice is frequently ignored. Even though our customers are aware that an IT firewall does not have the capability to recognize industrial protocols, which allows cyberattacks to take place at the supervisory or process level. It is a very worrying and high-risk decision as it leaves the system open to vulnerabilities and intruders.’ Firewalls that are used as solutions in industrial control systems not only segment networks into separated network zones to achieve vertical protection, but should also include the deep packet inspection engine function to filter unauthorized packets without affecting performance of operations and providing horizontal protection.
Tip 3: Adopt a Secure Communication Solution for Your Critical Data and Assets
The purpose of OT/IT network convergence is to collect data and transform it into valuable information. One good option is to utilize cloud technologies, which are convenient to use and have powerful data analysis capabilities, to simplify network convergence. A topic that has grown in importance recently is ‘How to secure your data access from OT to IT and from field sites to the cloud.’ ‘OPC UA brings a huge amount of security principles along with it’ said Ninad Deshpande, Product Manager for Cybersecurity at B&R Industrial Automation, (a member of the ABB Group perfecting automation and process control technologies). ‘This communication protocol not only features application authentication and user authentication, but also offers a security mechanism that meets the three pillars of security: confidentiality, integrity, and availability (CIA).’ When you are considering how to streamline communication from edge devices to cloud servers, OPC UA offers a reliable communication solution to ensure data integration is easy and secure.
However, when using cloud technologies, remote access poses a significant security concern. Increasingly, machine builders are leveraging cloud platforms to streamline machine maintenance. However, before you are able to reap the benefits, make sure your remote access is secure by using features such as data encryption and a VPN, as this will help keep your critical assets secure.

Now that we have considered how to reduce potential attack surfaces from the edge to the cloud for your connected industrial control systems, we will now focus on the people who operate these industrial systems and devices. Outsourced vendors, system integrators, and even remote service engineers are essential for daily operations, maintenance, and troubleshooting. They also play an important role to implement security policies. Any investment will become futile if these people lack cybersecurity awareness and do not know how to leverage these technologies. To avoid this undesirable scenario, it must be ensured that everyone involved in industrial processes have the same mindset and attitude to cybersecurity and only when this has been achieved will the results become apparent.
Tip 4: Enhance Industrial Cybersecurity Awareness From Management to Individual Levels
According to the security awareness pyramid, cybersecurity can be separated into different awareness stages. Commitment and support from management form the foundations, which is followed by security programs and policies being implemented during the awareness building process. Taking security policies as an example, it is fundamental to define who has Read and Write access based on the security configurations. However, when these policies are rolled out across an entire organization, it becomes a challenge to ensure everyone adheres to them properly. Facility managers often find implementing cybersecurity measures very cumbersome, and subsequently they do not ensure everyone follows the guidelines. Sometimes, they may end up doing things more akin to group level security, instead of ensuring each individual has their own unique log in credentials, and this subsequently opens up new cybersecurity risks.
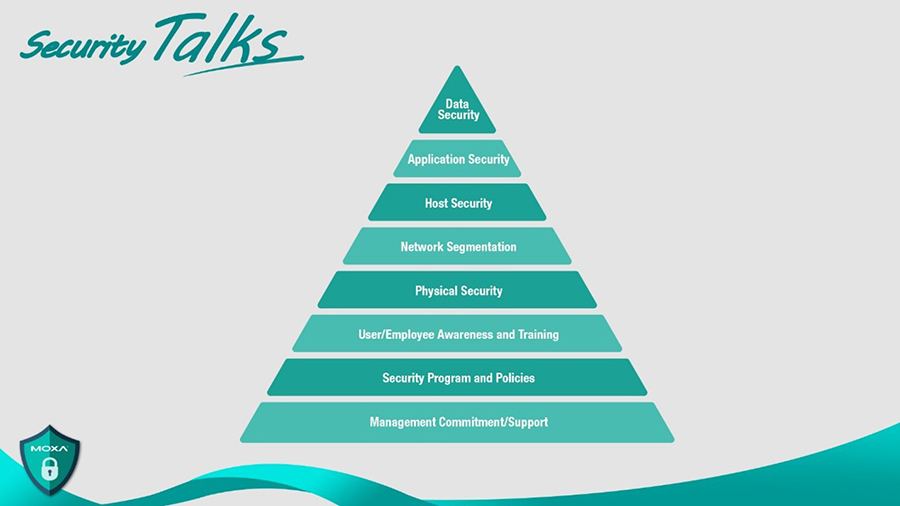 Diagram: Security Awareness Pyramid
Diagram: Security Awareness Pyramid
Thomas Burke works at Mitsubishi Electric Automation, which serves a wide variety of industrial markets with a family of automation products. Thomas has a wealth of experience in industrial automation and advocates the importance of increasing awareness and executing security policies in Moxa Security Talks. ‘Make sure the end-user, make sure the suppliers, make sure the employees really understand the different things that can happen and their important role in making sure that security is there.’
Tip 5: Examine the Configurations and Settings to Follow the Security Policies
Once awareness has been established and policies have been defined, employees will pay more attention to their system settings. We understand it can be a complex task to examine all the systems at one time. However, it is never too late to get started. Performing a risk assessment will help define security priorities and from this position it is easier to identify and protect critical assets. A good starting point is to examine configurations. If a large-scale network is being examined, it is recommended to leverage visualization software to check the security settings and adjust the configurations where necessary.
Reflection and Moving Forward
The popularity of the keyword ‘cybersecurity’ on Google Search will probably continue to increase in popularity in the near future since we know that organizations are trying to tap into the benefits of digital transformation and OT/IT convergence. There is no way we will be rolling back to the days of the past. That is why we hoped to offer a more holistic view by talking to multiple industry experts on industrial cybersecurity in this article.
- It is highly recommended to start with developing mindsets, formulating security policies, and systematically examining configurations.
- Once the groundwork has been performed, you can then start to look at secure edge connectivity to protect the mixture of new and legacy systems.
- It is important to remember to secure the network backbone that helps deliver the data that is required to achieve OT/IT convergence.
- It is also recommended to install industrial firewalls to consolidate vertical and horizontal protection.
- Last but not least, with the increasing demands on remote connections, a hassle-free secure remote access solution will save you money and effort.
If you wish to learn more, please visit Moxa’s microsite www.moxa.com/Security.